eloomi trusted
IT security
eloomi is 100% compliant with EU’s General Data Protection Regulation (GDPR).
Plus, we are audited and certified by Deloitte with ISAE 3402/3000/ISO27001 on hosting,
IT security and change management processes.
Secure infrastructure & process
eloomi takes personal data protection extremely seriously. Consequently, we maintain and continuously invest in high security and data protection standards. Every employee in eloomi knows our IT Policy and gets frequent training to ensure customer data is handled safely and securely. The eloomi infrastructure has been certified and is being audited to meet the most stringent requirements globally:
- ISAE 3402 Type II Microsoft Azure hosting
- ISAE 3000 eloomi Change Management and IT Policy
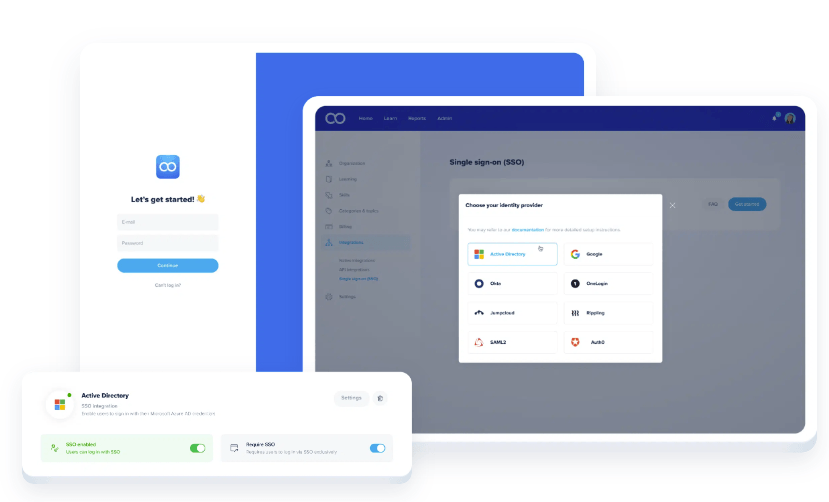
Password & SSO security
To keep the user access safe, eloomi enforces 2 factor authentication, where possible and requires strong passwords that match industry standards and requirements. Unsuccessful attempts to login will result in the user account being suspended for a specific time. If the login attempts continue to fail for a specific number of attempts the account will be suspended. Reactivation of the account then requires a manual administration procedure. In addition, user sessions, which are authenticated, expire when the user has been inactive for a specific number of minutes.
Single Sign On
Customers may use Single Sign On (SSO) which requires users to be authenticated via an identity provider. Other authentication tools or social login possibilities like Facebook, LinkedIn & Google can be used as well.
Personal data
eloomi handles personal data that is covered by the GDPR requirements. This data includes e.g. name, email, ID number and other unique identifiers.
No employees have access to confidential or personal data in applications and systems unless they are authorized personnel whose tasks and responsibilities require access.
Access permission including all temporary and durable access to IT tasks and job roles is the responsibility of and requires eloomi’s IT management approval.
The access control is documented for all applications, IT systems and environments giving access to sensitive information or personal data.
Mandatory criteria for managing access rights and control via Access Control Lists comprise:
- Overview of user roles and access profile
- Process for adding, changing and revoking access rights
The right to be forgotten
Users can be confident that their personal data has been backed up in accordance with GDPR principles of privacy by design and the right to be forgotten.
The right to be forgotten is a main pillar in GDPR. This principle, which makes it possible to identify the location of personal data – either all company data or individual user data – and to delete or anonymize it, is incorporated in all systems and processes.
It is possible to choose how long it will take before deleted users are anonymized. By default, deleted users are automatically anonymized after 72 months.
Audit logging
Another major change imposed by the GDPR is the audit logging. To make sure eloomi and our customers are compliant with the regulation, our systems keep track of who (users, admins, operators) views and edits data. Unsuccessful user login attempts are also logged. Audit logs are stored for 5 years in a safe place with restricted access.
